High Assurance or “Extended Validation” EV SSL Certificates
Here's an excerpt from a "mid-level" educational/nutshell whitepaper I'm doing on the new shiny SSL certificates that are coming soon. If you want information from someone who REALLY knows what they are talking about, subscribe to Tim Callan's SSL Blog. Also, watch the IEBlog. If you're running IE7, you can download and install a sample testing certificate then visit the fictional https://www.woodgrovebank.com and see the new certificates it in action.
ASIDE: On a totally different (but, eh, slightly related) note (and I'll blog or Hanselminutes.com about this later), if you're running IE7 and .NET Framework 3.0, check this out.
SSL - Secure Sockets Layer
What is changing?
Every online banking site protects their user’s data while it is in transit on the wire using Secure Sockets Layer or SSL, running one layer below protocols like HTTP and FTP. Many end users are informed enough to look for the “s” in HTTPS in their browser’s address bar and most look for a lock in the browser status bar before sending private data across the Internet.
Early versions of SSL used comparatively weak 40-bit encryption but most sites now use at the very least 128-bit and in some cases, 256-bit AES encryption. Many impose this important restriction by default by allowing only SSL3.0/TLS1.0 over HTTPS.
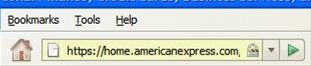
This screenshot from the Mozilla Firefox browsers shows that the encryption strength of two different banking sites. This dialog is reached by the user clicking on the lock icon within their browser.
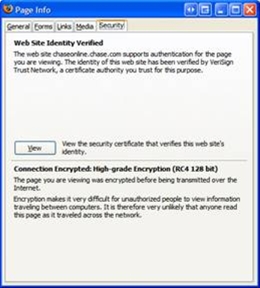

In these examples, both sites are using high-grade encryption.
Recently more and more phishers have been successful in fooling the public into giving up personal information with the use of so-called “domain-authenticated SSL Certificates.” These SSL Certificates go through virtually no background check to prove the site is who they say they are. They prove only the domain name, but as the general public rarely clicks on the lock icon to view more information about the company or organization behind a SSL connection, they assume that a secure connection equals a trusted connection. This, of course, is not the case. Unfortunately these SSL Certificates look essentially the same to the browser as one issued by a highly trusted certification authority, thereby causing a phisher’s site to look “as secure” as your bank’s site.
High Assurance or Extended Validation SSL Certificates are a new kind of SSL certificate that will be treated very differently by newer browsers. Internet Explorer 7 will be the first browser to take advantage of this new technology with others like Firefox and Opera very close behind. This standard is being actively developed by the CA/Browser Forum as of this writing and will be referred to commonly as EV SSL Certificates.
To quote from Tim Callan’s SSL Blog at http://blogs.verisign.com/ssl-blog/2006/03/a_new_kind_of_ssl_certificate_1.html:
If every Internet user in the world had a browser that recognized the difference between High Assurance SSL Certificates and traditional ones and if every legitimate site used a High Assurance certificate, then phishing as we know it today would essentially be eliminated.
A lofty goal indeed, but one worth striving for.
How will an EV SSL Certificate change the end-user experience?
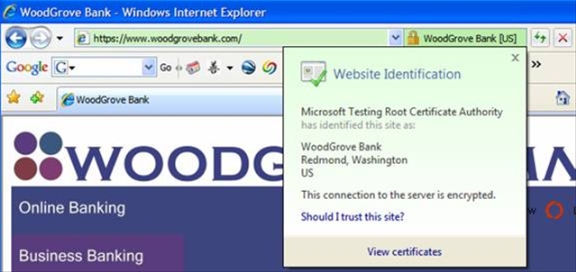
When visiting a test Banking Site that has an EV SSL Certificate using IE7, the address bar turns green and a new active lock icon appears showing the name of the organization this site claims to be.
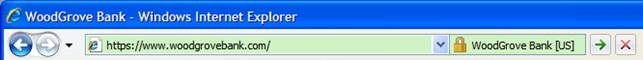
The lock icon toggles back and forth also showing the Certificate Authority that issued the certificate.
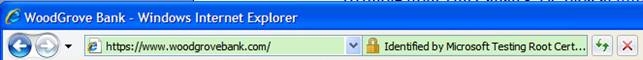
If the user clicks anywhere in the secured area of the address bar, the identifying EV SSL Certificate popup is green and shows the user information they can use to make the decision to trust this site or not.
What is required to get an EV SSL Certificate?
As of this writing EV SSL Certificates are not yet available for purchase, but they are expected within very soon as the standard is finalized. Within a year expect all major browsers to support the standard and within another year most e-commerce users will know to watch for the new browser behaviors when making their decisions. I predict some browsers will have settings that will only allow users to visit sites over SSL that use EV SSL certificates.
Educate your organization about the importance of having an EV SSL certificate when they are ready to be issued, and be prepared to meet the much more rigorous standards that will be expected by the Certificate Authority before they issue one. There will likely be a revised Certificate Authority WebTrust auditing standard (usually called CA Web Trust) that CAs will have to pass before they can issue an EV SSL certificate, and CAs will impose much stricter vetting procedures to verify the company or organization requesting the certificate is who they say they are.
Conclusion
Given the concerns on today's Internet around privacy and control over content, every e-commerce or banking site should be prepared to upgrade their SSL Certificates to EV SSL. There's no downside.
About Scott
Scott Hanselman is a former professor, former Chief Architect in finance, now speaker, consultant, father, diabetic, and Microsoft employee. He is a failed stand-up comic, a cornrower, and a book author.
About Newsletter
I bet having a big wallet is one of the extra checks.
I'm assuming this is a purely browser/server issue still rather than anything needing to be done within the application to support this. No new html tags etc.
If appropriate, can you comment on whether Corrilian provides certs with your product or whether you leave that to your customers to solve (along with any consulting services you're providing)? Would this change with EV SSL for any reason?
1) it adds yet another point of confusion that will be a problem for non-expert users. Note how long it took to get users to understand the importance of the lock icon in the first place, and even that is by no means even nearly universally understood and properly acted upon.
2) the new 'enhanced' assurances are the type of thing that I believe most users expected to already be happening with the current cert scheme. Isn't that what CA's are for? Even though I know nothing about the proposed processes for issuing these new certs, I'd be willing to bet that within a few months of their general availability someone will obtain a bogus one (either for actual fraudulent use or for simply demonstrating that the system is pretty much as vulnerable as the current system).
Another (probably bigger problem) is the fact that IE through version 6 and FireFox through version 2.0 do not provide any special support for the new cert types, so for quite a while this will mean absolutely nothing for a bazillion users.
CA's should have been doing their jobs correctly from the start.
Ian - Other than being able to prove they are a legit business, no, the business owner doesn't have to do anything technically to make this happen. Corillian doesn't provide certs, but we do make recommendations to our clients about which certs to buy. We will recommend EV SSL to our clients.
1) How many startups actually charge for things right off the bat anyway? We could discuss the problems that causes all day, but a 150% (via Tim) increase isn't going to break any bank, certainly not a VC funded one.
2) Even if we assume an increase in startups that charge for stuff, It's just not in verisigns interest to screw people any more than anyother company, they make money selling certificates and dime a dozen startups are good money for them, why on earth would they want to stem that flow?
3) Anyone not funded, and too poor to buy a certificate can certainly use a company like paypal to solve any charging issues they have, which also saves them running their own commerce site.
I'm with Scott (with a nod to Mikeb) I don't see a downside apart from the confusion/ 'wasn't this happening already' issues.
This 'new' technology will be secure and closely checked for a while, but market forces are likely to do exactly the same thing to this spec. Once it spreads out the validation will get lax and we're right back where we started.
At my company, we have line of products that we will provide in a hosted solution environment for the clients that don't want to run their own servers. Each hosted client has a sub-domain with it's own certificate (issued to my company). If you check out the details, you will find out our legal name and location--including street address.
If a phisher wanted to spoof one of our installations, they could probably get a similar domain name, but their choices are limited when it comes to spoofing SSL (assuming we had been using these new certs):
1. Use an "old-style" domain authenticated cert. The address bar doesn't turn green and our users are tipped off.
2. Use a "new-style" cert (that must be fully authenticated). Their location (and hopefully address if the spec is done right) shows up in the browser. Our users are quick to notice that OUR business name doesn't come up in the address bar, so they don't log in and they let us know immediately. When we find out, we happily forward the info to the FBI.
I realize this is a pretty utopian view of how our scenario would work, the phishers could get a business license or DBA with a fraudlent name/address (which I hope is tough to do, sorry I'm not an expert on how to perpetrate "real-world" crime ;), the users might not notice the business name change (or even the address bar color), etc.
What I think we need to strive for now, short of a perfect solution, is to do anything that would act as a deterrent to would be cyber-criminals. Anything that would stop the "small-time" ones and even slow down the "big-time" ones is a good thing in my book. The world seems to be full of naysayers that don't offer solutions, just pick apart others' attempts to solve problems.
That's sloppy. Microsoft should have at least filled in all the fields.
Comments are closed.

I'm afraid this will be a good excuse for for Companies like Verisign to rip people off and try to regain a monopoly on the market.
It does not seem to me that the backgroud auditing of the companies is related to the technology of the certificates.
I'm afraid that by mixing the two, it will confuse even more the average people.