Technology fails in film are the new Wilhelm Scream
 There's no other explanation. It must be a tradition like the Wilhelm scream.
There's no other explanation. It must be a tradition like the Wilhelm scream.
What, haven't heard of the Wilhelm scream? Well, once you do it's impossible to not hear it in every film. It's in freaking Lord of the Rings, and it grates. It's THE go-to person screaming sound effect and has been for over 50 years. Here's a compilation of dozens of movies - including every George Lucas movie - that uses the Wilhelm scream.
Hollywood and TV seems determined to make the technology-aware jump up from their seats and scream NO!!! at the screen.
I can only imagine what a doctor or nurse must feel like when watching ER or a dramatic surgery.
A technical error pulls me out of the story like a slap in the face. It almost physically hurts. I'm not just nitpicking here, either. These aren't hard things to fix. One just needs to care.
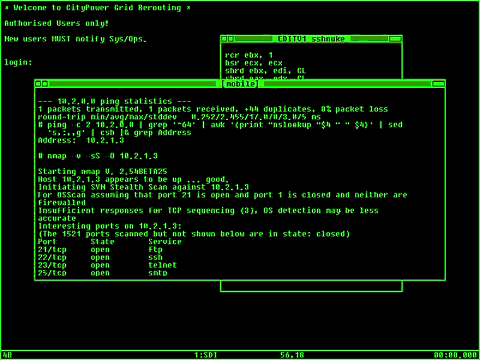
Now, often they'll use internal IP addresses to represent external addresses and a lot of folks argue that using these addresses is the "555 Phone Number" equivalent. I can see that a little, but even if they used the IP Address of the studio it wouldn't be so jarring.
It's debatable who is worse between TV and Movies, but it's clear that CSI has the #1 spot locked down with this classic.
GUI interface in Visual Basic
This is so cringe-worthy, it's legendary.
Jurassic Park It's a Unix System
I wish all my file systems were in 3D. This was actually a real UI that you could use. Bummer that ls -alogF isn't as photogenic.
Bing it? Hawaii Five-0
Bad product placement (IMHO) is becoming a problem on TV as well. While this isn't inaccurate, the cheese-factor here is high.
Red Dwarf UNCROP
I personally love this video and while it's techno-nonsense today, I'm sure the next version of Photoshop will have this feature. Those guys are amazing.
The Net Hacking
What can I say about this other than I am nostalgic for 3.5" floppies.
Hackers Script
I have to admit that I love Hackers and it's amazing to watch a young Angelina Jolie and Jonny Lee Miller. You can read the script online. Nearly every technical detail is sketchy, though.
SkyFall
I found SkyFall to be very entertaining. The folks at io9 have a nice post on the hacking scenes. I love this;
"...at one point Q exclaims, "It's security through obscurity!" as if this is the most elite thing a hacker could ever do."
Sigh. Wouldn't it be great if a movie producer reached out to us to help?
NCIS - Hacking Gamers
Oh, CBS.
SwordFish - Giant Monitors
Most of my great hacking moments include 6 monitors on arms, dancing and a dynamic montage, don't yours?

NCIS - Two Idiots and One Keyboard
NCIS keeps bringing the hits with a keyboard maneuver that needs to be seen to be believed. "I'll just ASDF and you can JKLsem, ok?"
Chloe, open a socket
Chloe from 24 is always asked by Jack to "open a socket." There's a lot of questions on the net wondering what this cryptic tech-speak means: Can someone tell me what a "socket" is? "24" NO Spoliers [sic]!
There's even a band called Chloe's Open Socket. Awesome. http://www.chloesopensocket.com

SwordFish
Want to know what it's like to hack like SwordFish? Visit http://hackertyper.net. ;)
Antitrust
Here's not one, but two classics from Antitrust.
The Matrix
Sometimes I need to just re-watch the nmap hack in The Matrix to cleanse myself. It was so refreshing to see real commands and a real hack in a movie that we already respected for it's attention to detail.
Sadly, this hack is now the go-to hack for movies that care enough to steal their hack but don't care enough to research their a new one.
What's your favorite horrible technology FAIL in film or TV?
Do you think that all this is being done a purpose, like the Wilhelm Scream?
Sponsor: Thanks to Red Gate for sponsoring this week's feed. Free eBook – 50 ASP.NET & SQL Server performance tips from the dev community, to help you avoid, find, and fix performance issues in your ASP.NET app. Download it from www.red-gate.com/50ways
About Scott
Scott Hanselman is a former professor, former Chief Architect in finance, now speaker, consultant, father, diabetic, and Microsoft employee. He is a failed stand-up comic, a cornrower, and a book author.
About Newsletter
The GUI in VB scene (I'm assuming it's CSI) isn't actually that implausible in the policing world.
I've done exactly that a few times to help detectives go through some hideous task. Every detective has Access on their computer so it's far quicker to crank out something quick and dirty in access, and know it will run on their machine, rather than worry about what flavour of .NET they're running on.
Perhaps real time tracking of IP addresses using VB is a a bit daft though.....
https://www.youtube.com/watch?v=F5bAa6gFvLs
Hackers Techno Babble as they read of hardware specs for laptop.
https://www.youtube.com/watch?v=jwg4mbGL4JE
Most TV series that mention games in any way. Like the NCIS above, they seem to think that MMORPGs are exactly the same as multiplayer DOOM and Unreal Tournament. They also seem to think that games are completely hackable by any uber-player.
My big gripe though is when the cops or FBI set up a huge amount of tech gear to trace the call from the kidnappers, and the trace taking at least 30 seconds to complete. Modern phone exchanges are a little different from the old days of rotary or switchboard connections, and know the number, address, and name of caller the nanosecond the call is made. All the police need to do is ask the phone company (may need a warrant first.)
I loved it so much I took a screenshot - http://twitpic.com/7l87fw
https://www.youtube.com/watch?v=HyDXEik3mH8.
You see a guy furiously pounding a keyboard and then about 38s into it you see that they forgot to remove the Window Media Player sidebar :-)
Hence, I formally protest to the inclusion of that clip alongside abominations like Swordfish and *gulp* Visual Basic GUIs.
If the clip should remain on this page then only as a prime example how inclusion of technology in movies or TV is done properly.
It isn't an expensive endeavor either, most would be willing to do it for nothing more than credit on IMDB for goodness sake. After all, we're already well compensated so we don't need money. What we do need however is some "cool points" for our class reunions.
http://www.siliconbunny.com/fsn-the-irix-3d-file-system-tool-from-jurassic-park/
It might not be useful, but it _is_ real.
I feel if you're gonna complain about this stuff, at least get it right.
Here are some more things I find very strange:
- Hardly anyone uses Windows, OSX, Ubuntu, or any of the other known OS's. They all have a custom OS.
- If a system is secured with a password, usually you can guess it in two or three tries. If not, you call someone or enter a couple of commands to make it go away.
- "Hackers" with 5,6,7 up to 10 screens. How do you look at ten screens?
- Some laptops have a big Windows logo on the back (product placement). Have you ever seen a laptop with a big windows logo on the back?
- USB sticks don't exist, Everyone has an obscure thingamabobby. Funilly enough, these obscure devices connect to all other devices without a problem.
Must of these don't really bother me, but some are just so over the top that it decreases the show's believability.
Independent on the size of the image you can zoom in to see every little detail and recognize everybody. If it's blurry, you can just "enhance" the image and it will become crystal clear.
- Kenneth just said my favorite where any image can be "enhanced" to see amazing detail.
- The network of ATM, traffic, and security cameras that law enforcement can tap into and using awesome facial recognition software find people nearly anywhere in the world
- Also said by somebody else, any password is easily cracked
Actual detective work is no longer needed as the technology does everything.
Although, interestingly, as John as pointed out, the only technology writers make less sophisticated is that magic 30-second timer on tracing phone calls.
Of course, that was around season 3 or 4, so can't say whether later seasons jumped the shark.
The rest seem good, and entertained me. Just can't let anyone rag on my Red Dwarf.
the theory was this hacker had to store his secret accounts on one of his pc's. an xbox is like a pc. therefore he may have stored his secret files on his xbox console. (this makes sense)
therefore to read his excel spread sheet we must first finish the first 8 stages of prince of persia and then the spreadsheet magically appears on the tv.
what the hell.
so whenever this dude quickly needed to update his figures all he has to do is finish a game quick.
(Mashup of my faves from The Net & Hackers...)
:)
- Jack
The entire 'Back to Earth' was one massive Blade Runner homage ("I just do noses...")
Hollywood is focused on A) telling a story to a mass market and B) repeating the process that worked last time. Inaccuracies only 'hurt' those who know the truth and if an inaccurate portrayal tells the story faster, in a way that's less confusing to Average Joe then that's what Hollywood will use.
But don't worry, technology is in no way singled out. Everyone and everything represented on the screen is modified or fabricated to serve the story.
Unfortunately, with the exception of Red Dwarf, I think all of the other clips you've shown are trying in earnest to represent computers and computer security in an exciting way, and just completely fail.
Yes they probably should ask "us" for a little bit of help. I mean, House M.D. consulted with real doctors for all of the medical diagnosis stuff. From what I understand, it's realistic/plausible (with the exception of the compressed timeline).
It'd be different if *every* movie or tv that was about to show some magic hackery would start with the character saying "It's a unix system, I know this!" Then we'd know it was an homage/joke, as opposed to just lazy production.
That apart, you guys are talking about Hollywood films, if you see some of the regional films we get in India, you will probably cry to death as I have many a time. A sample from a South-Indian film is provided for your perusal.
http://www.blinkenlights.com/classiccmp/portfolio.txt
http://en.wikipedia.org/wiki/Atari_Portfolio
As for intentionality. That's the question. Is this incompetence or an inside joke? I think it varies.
No one does.
Interestingly, this applies to both IT stuff and hospital stuff.
In real hospitals, no machine is ever going bip all the time. Heart monitors going bip at every heart beat get very annoying very fast. In fact, even the alarms are sometimes off (but redirected to the nurses stations obviously).
https://www.youtube.com/watch?v=nTI0ovUMnyE
It would be pretty ironic if a comedy show got it more often right than anybody else.
I love watching Dexter. But his AFIS Mobile finger print app on his iPhone in S07E01 was a bit too much for me :-)
image
But at least he has a real iPhone now, not one of those fake phones they used in earlier seasons.
Also: when they use iPhones that say BEEP when they hang up a call, or when the display is clearly still on when they hold it to their ear to "call". :-S
http://www.youtube.com/watch?v=m4SBMyd0yEQ
Great movie, by the way.
http://boingboing.net/2011/04/06/how-emacs-got-into-t.html and http://jtnimoy.net/workviewer.php?q=178
- The auto-complete shows only the one result she is looking for, and no other results.
- The auto-complete shows "clifton bowles" after she has entered "cl" and nothing more.
- After glancing at a word-heavy page of search results, she instantly has her answer.
Not even Bing is that good.
"The painful part is that there is a large group technically sophisticated folks who would love nothing more than to fact-check these scripts.
It isn't an expensive endeavor either, most would be willing to do it for nothing more than credit on IMDB for goodness sake. After all, we're already well compensated so we don't need money. What we do need however is some "cool points" for our class reunions."
I have an acquaintance who's a screenwriter, and I've actually been invited to do such for some scripts. It's a lot harder than you'd think, simply because directors and producers aren't going for perfect accuracy...they're going for telling a story in 42 minutes (or 2 hours in film). Every time I've done it, it's turned into a negotiation of "Okay, X is inaccurate but you have to do it because it interrupts the pacing of the story and you can't film it. I can accept that. But for God's sake, Y is over-the-top stupid, find a better way."
Like the NCIS "Two Idiots, One Keyboard"...I'd have said "You can't. No. Don't do it. Put a second keyboard there. You still get to demonstrate the characters are close and work well together, and it's far less stupid."
And I'm likely to be paying WGA dues before I ever get an IMDB credit. Credit is jealously negotiated.
1. He has access to everything. (On the show, he claims to have spent the last decade getting backdoors into everything. Given what we saw with the British hacker complaining that the Chinese kept kicking him out of the Pentagon computers, it really doesn't sound that far-fetched.)
2. He does everything with a phone given to his associates. Given that phones have Wifi and Bluetooth, and given the number of devices that are insecure on any given corporate network (easily-guessable passwords, etc.) is it really that far-fetched that you could hack a lot of stuff with a phone?
Setting off all the car alarms in a parking lot was a bit much (fire that writer), but I feel like in general it was a pretty good portrayal.
That and any covert explosive device that beeps and has a massive bright LED on it!
The amazing, animated, bowling sound-effect CRYPTO-SMASHER V3.10.
http://www.youtube.com/watch?v=5z3SGMbICsA
Numb3rs' description of IRC
http://www.youtube.com/watch?v=O2rGTXHvPCQ
Some image editors, when saving a modified image, leave the thumbnail from EXIF metadata unmodified; so technically you can recover that thumbnail later and take a peek at the original image.
Here's a demo: http://www.youtube.com/watch?v=ielWCOjZYfM
Again, the rest is resolution nonsense
What digs at me the most is the relationship between everything in a network and the magical, mystical and misunderstood "Mainframe".
As in "Move fast people! We've only got about 30 seconds before it reaches the MAINFRAME!!!!"
-Rob
I assume you know this. You can open a "socket" in Java to obtain an input/output stream to an external IP.
I've never seen the show to what lunatic why they are using it.
Also 24 loved to use IP addresses starting with 292
http://m.youtube.com/#/watch?v=ez5XSc8AMKQ&desktop_uri=%2Fwatch%3Fv%3Dez5XSc8AMKQ
On the flip-side of this topic, I love it when someone goes the extra mile to be accurate. If anyone is a fan of David Cross (and who isn't?), watch The Increasingly Poor Decisions of Todd Margaret. There's a scene where he pretends to be deaf and is faking sign language.
In reality, he hired someone to teach him some sign language and is actually signing some very obscene messages.
I've watched every episode of Big Bang and from what I can tell they have very good technical / geek consultants. I haven't face palmed once.
https://www.youtube.com/watch?v=D92hau35NyY
Put in an IPS signature that black holes the pattern
...
That'd be resistant to false positives too
I agree with the comment about connecting a machine to the local network, at which it infects everything, instead of actually making an image and using forensics tools.
- At the end of War Games, when the WOPR is trying to guess the nuclear launch codes. It needs to figure out a 10-character alpha-numeric code and despite the fact that it can tell when it has the correct character in any one position, this takes more than the 36 iterations that the simplest brute force algorithm would need in the worst case.
- At the start of Disclosure, Michael Douglas opens an email. The on-screen process starts with an envelope sliding out of an in-tray, into the middle of the screen. It then opens and a piece of paper slides out and unfolds. The contents of the email are then typed one character at a time. Surely it would be quicker to go back to using paper!
A guy who makes the fake OS programs did an AMA too - all of the fictional app/OS stuff is built in Flash and there are just a handful of contracted shops that do all TV shows. It doesn't pay well and is usually last minute - another reason to not put a lot of care and correctness in.
which essentially is the same as smashing a hole through your television to get to the movie / tv-show that is currently playing.
They test their plan in a highly graphical computer simulation which is shown to be controlled via a Commodore 64.
As if this isn't hard enough for us to believe - the camera pans around to reveal that it doesn't even have any power/monitor connected to it.
http://nmap.org/movies/
I really crack up how the mouse doesn't play much, if any, of a role in on-screen computing. Although, Office Space did a good job of showing that. :)
When it gets down to it, today's movies still have a lot of similarities to the 50's Sci Fi movies. There are a lot of blinking lights and lots of noisy bleeps, blips, and bloops.
The fact that I still manage to enjoy that film despite a few of these ridiculous techfails is a testament to how well dont the rest of it is.
Never-mind the implausibility of it... BATMAN DEVELOPED IT! Freakin' BATMAN!
In that hacking scene (or just before, I don't really remember), to "prove" that they are at the top of their game in the IT department, the little genius plugs-in TWO network cables to its computer. Because one is never enough.
It made me laugh so hard ... Completely killed the scene for me. :)
Very entertaining blog post, thank you scott :)
in the red dwarf clip, i understand that its "future tech" ....
but how are you going to "uncrop" something that isnt there in the first place? .....before someone decides to think of a response, realize this, the guy picks up a printed physical copy of a picture that was cropped (that means the sides of the photo was cut out for those that dont understand) and magically poof's it into reality...where did they get it from again? and if people dont understand this and resolution, ofc its going to be fantastic (havnt seen nor am i talking bad about the rest of the series)
now picking apart a little of CSI. Seriously? she is going to "create a GUI interface to track what? an IP address? ok....not saying its impossible.....but that implies that she is a programer for one, and that she must of have some sort of grasp of how long this will take (which is anywhere from many hours to at least a week), illigal in a way that it means the ip address (you know, Internet protocol) which is infact something that usually a business takes care of, like comcast, knology or something of that nature, can be given with proper warrent by said company and since they arnt, means they are just taking it without regards to rights and other laws, and god forbid if the person is using a computer at an enormous building with 100's of computers or an internet cafe with free wifi. now having said that, if they really need to track IP addresses, there probably is already an application or program out there already....
just throwing that out there.....
http://imgur.com/zXR0qAN
http://youtu.be/_wwYtgQHFV8
http://www.stuteriveterinarerna.se/sendmeil.asp?p=80 http://www.stuteriveterinarerna.se/sendmeil.asp?p=80
Comments are closed.