Ten Things To Do to Secure an Important Person's Computer (or even Ashton's or a Kardashian's)
I have a some friends and friendly acquaintances who are of some bit of note. Not Internet-famous, or even blog-famous like me, I mean actual famous. Like us, celebrities still have phones, Twitter accounts, Facebooks, laptops, hard drives, family photos and lots more that need to be managed. Maybe you're fancy also? Maybe you think you're fancy or just want to be?
Sometimes I spend time on Skype with my friends going through a list of things they need to do to cover their butts when it comes to their personal media and gadgetry. I thought I'd make up a list that I could send to them as it's become repetitive, then I realized that this stuff is important to all of us, not just folks on TMZ.
Apparently Famous People have Other People that tell them what to do, but it's unclear if the Other People actually know more than the Famous People. I know, Kim, you have no password on your Macbook and no encryption on your phone. Let's talk.
1. Find Your Phone - Make your cell phone "findable"
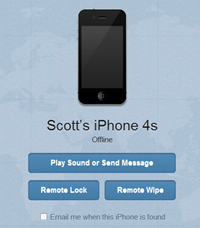 It flat sucks to lose your phone.
It flat sucks to lose your phone.
- If you have a Windows Phone, you can go to http://windowsphone.com/my to locate, ring, lock or even torch your phone. It just works and it's on when you setup your phone for the first time.
- If you have an iPhone (or any iDevice, in fact) you can go to http://icloud.com, sign in and locate, run, lock or wipe your phone as well. For offline phones, you can have it email you when the phone is found (turned on). You'll want to update your iPhone to iOS 5 and run through the initial wizard in order to confirm this is working for you.
- There's a dozen or more choices for Android phones, but I suggest you check out either Plan B or Where's My Droid. A third good option that you could use on all your devices is Prey. Each of these will do what they need to. Find your phone.
Test your chosen Find My Phone technique before you go off losing it! Make sure all your stuff is backed up occasionally so you won't feel bad at all about a Remote Wipe (erasing your phone so the bad guys don't get it).
Add a Pin Number and Lock Your Phone
Next, DO Add at a Pin Number or password to your Phone. Having a phone that's unlocked already is just asking for trouble. You can always pick a simple 4 digit pin but pick SOMETHING.
Make an "If Found" Wallpaper
However, if you do use a password or pin and lock your phone by default, be sure to update your wallpaper to include contact info. I highly recommend the application If Found+ for the iPhone. It'll take your existing WallPaper and stamp a "If found, call..." or "Reward if found, email..." on your phone. Sometimes $50 and a phone number will get you your phone back quickly.
2. Don't be Trackable - Turn of Location Settings for specific apps on your Phone, Twitter and Facebook
You want to be able to find your phone, but you shouldn't give away your location when you talk online. Ever heard of http://pleaserobme.com? They'll look at your Twitter account and see if you're giving away your location via FourSquare checkins and the like. The bad guys would love to break into your house when they can be sure you're not there. Broadcasting your location is a great way to make it easy for them.
There are many ways you can accidentally give away your location. First, in your Twitter profile. Early iPhone Twitter clients would update this field automatically with your exact latitude and longitude.
For example, here's a parody account that indicates it's not a real person. However, I can still tell where they are in the world...down to 6 decimal points.
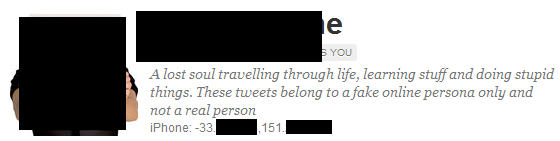
Another way is to tweet and include your location, either on purpose or accidentally. Most Twitter clients have a "geotag" button now, but you may just want to turn that feature off completely by denying the twitter application access to your Location Services.
Also, don't be the mayor of your house. Foursquare recently started "blurring" the locations of what it believes are residences, but you can still give your location in general terms when you check into a home or residence.
3. Lock your Laptop - Secure your computer (desktop OR laptop)
I amazed at how few people even bother to put a password on their laptops. Yes, there's always a way to break a password or get information off a hard drive, but why make it easy for them? The main concern is that if you allow anyone to boot up your computer and run a web browser, chances are that you've clicked "Save Password" on your Facebook or Twitter or, even worse, your email. At that point you're dead.
Consider installing PreyProject on your machine. It can make it possible to track your laptop or desktop if it's stolen. There's been a number of times where folks have been able to track a thief in real-time and secure their belongings - while live-tweeting the whole event!
4. Encrypt it ALL - Secure your personal files and external hard drives
Here's an experiment that will scare the crap out of you. Use your computer's search function (upper-right corner on a Mac and lower-left on a PC) and type in your Social Security number. Go ahead, it's not going to the internet. See if you find some PDFs from your accountant or an old Excel file. Freaked out now? Now either delete it or put it somewhere secure.
If you have files with information you don't want falling into the wrong hands, consider using a tool like TrueCrypt to make an "encrypted volume." This is a single file that you can access as if it were a disk itself. You can make a "personal.dat" file of any size and keep your personal information inside that "disk inside a file." You can then keep that file in DropBox or another cloud storage system. With a strong password, these TrueCrypt files are VERY VERY secure.
If you have a technical friend with you, you can even encrypt your entire disk with TrueCrypt. Or, if you have Windows 7 Ultimate, you can "bitlocker" it, as I do all my drives. This way, even if a bad guy gets your laptop, they can't do anything with your drives. They are bricks without passwords and pins.
5. Don't Carry Your Life in Your Pocket - Encrypt USB Keys and "Jump Drives"
Some folks will take precautions with laptops and computers but then copy their whole life to a portable USB stick and put in their pocket.
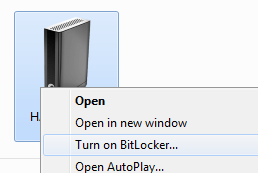
If you can, encrypt your files on your portable drive - again, with TrueCrypt or BitLocker.
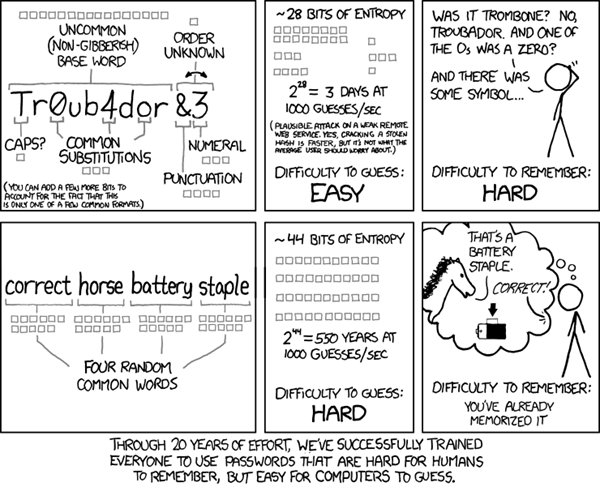
6. Use Better Passwords - Make it harder, or use Pass Phrases
Using the name of your last movie or the street that you grew up on may seem like a clever password but it's not. A lot has been said online about password strength, so I won't belabor the point.
If you can, use a passphrase that's longer than a password, but easier for you to remember.
7. Super Secure your Email - Turn on 2-factor auth in Gmail
After you have a great password, if you've got a Gmail account for example that you REALLY can't have compromised, consider turning on "two factor authentication."
Hang in there, Kim. Sounds scary, but isn't. Two factor means, two things that you have or remember. A password is just one thing you have to remember. It's one factor. But two factors means a password plus something else. The second thing will be something you have.
You always have your phone, right? So why not make it so your Gmail account requires a password (that you know) and your phone (that you have).
- To set this up in Gmail you go to using 2-step verification.
- You can turn it on and give it your cell phone number. You can then install a small application that will give you a code that you'll use as your second factor when you log in. "But, wait, that sucks! I don't want to do that every time I log in!" Don't worry, darling. You don't have to. You can tell Gmail to only require this code every 30 days.
- If you have other services, apps, or maybe your phone's email that use your Gmail password these will suddenly think the password has changed because they don't understand two-factor auth. For these applications, you'll just give them their own custom password.
- You go to manage application-specific passwords and get a password or two for your phone's mail or other apps that need Gmail access. The nice thing is that each app gets its own password so you can revoke them at anytime!
You can also tighten up your Facebook security by turning on Login Approvals. This is effectively two factor authentication as well. Facebook can SMS (text) you when you log in and then you type in the number they send you to confirm that not only do you know your password, you also have your phone.
8. Hide Where You Live - Make sure None of your Domains have your Home Address visible
Make sure if you own a domain that you've turned on Privacy or use DomainsByProxy or some other "WhoIs Privacy Protection." You don't want a fan showing up for dinner.
9. Secure Your Login - Turn on SSL/HTTPS for Twitter, Gmail and Facebook
If you find yourself in a Starbucks or on location a lot using strange Wi-Fi, you should probably make sure that your Twitter and Facebook accounts are using https (the S is for more Secure) by default. That's the same kind of encryption your bank uses. Just check your Twitter and Facebook accounts. You only need to do it once.
Here's Twitter:
And Facebook:
You can also Google more securely at https://encrypted.google.com or https://duckduckgo.com.
10. If it starts with HTTP, it's probably public - BTW, TwitPics are Public
If you use a tool like TwitPic or any online photo sharing, or - let's just be straight here - anything online...it's likely public. If it has a URL, someone can get to it. Assume everything you do online is public.
I've personally watched a number of celebrities have conversations between each other on Twitter as if Twitter were a private chat. Just last month Charlie Sheen tweeted his phone number to Justin Bieber. So, he got a new phone. http://3109547277.com
Also, just an FYI. Don't take a picture of your pee-pee. There's just no reason for that.
Conclusion
This may sound like a lot, but it's simpler than you may think and it can be setup so that it's not invasive in your life.
The main points are these:
- Make it so you can find your stuff, but others can't find you.
- Use pins or passwords on your devices when you can.
- Encrypt sensitive data in TrueCrypt files or Bitlockered drives.
- Use "two factor" authorization for crucial services like email.
Feel free to suggest other tops I may have missed in the comments! And, perhaps pass this on to your Famous Friend.
About Scott
Scott Hanselman is a former professor, former Chief Architect in finance, now speaker, consultant, father, diabetic, and Microsoft employee. He is a failed stand-up comic, a cornrower, and a book author.
About Newsletter
One thing that I would add to your list is that you should have a password to the BIOS. That way even if the thief swaps out your hard drive they can't use your laptop. With fingerprint recognition this is no longer an inconvenience on HP laptops.
- Switch your voicemail off (O_O - yes @rupertmurdoch I am looking at you)
- Obvious one that I'd assume famous famous people do already but... Have fun with your email addresses, etc LordCoffeeCup@gmail.com, lordy@sprokets.com etc.. instead of barack.obama@whitehouse.gov
- Following on from that, get the geek in your life to show you/enable easy switching of email addresses when you'd like to use a fresh one.
- We all have Palin moments of brain failure. So don't make your three account security questions answerable from your wikipedia page.
=)
Great tips. Thanks very much!
Jonathan
Locking a Windows machine is easy: Windows key + L. DO IT! NOW! It has prevented many pranks on my laptop in college.
If you've lost your phone but you're still within earshot, http://wheresmycellphone.com/.
Similar to the classic SatNav story, where a car was stolen and the thief used the sat nav in the car to take him to the victims house.
You have to be especially careful these days.
Chris - You caught me!
No point me taking precautions to avoid broadcasting my address if my friends do so on my behalf.
It boggles my mind that people don't use passwords on their home PCs. I go as far as to use 2 accounts, an admin account that I never log in to and the user level account that I use every day. Each has their own password and when I need to install something I just click to run as administrator and put in the admin account password into the dialog. It mimics Linux somewhat, though they handle it much more seamlessly than Windows in my opinion. I never worry about self-executing viruses as I just don't need to give the admin rights to install it. I still have Malwarebytes and Security Essentials though.
Excellent article all around!
Just to add on point #9 - You can use a Personal VPN connection when using "public" or "free" WiFi
(Sorry for the very minor nitpick. Excellent and informative, otherwise.)
http://bit.ly/u5ahiR
you can turn off/uninstall not-needed antivirus part out of it and keep excellent tracking one. They acquired Theft Aware while ago which was arguably the best anti-theft android software, and now it only can get better.
Pros:
- AVAST! is a big&trusted company with years on PC market (actually the very best free AV on Windows in recent years) not some 'unnamed new chinese android company' - i.e. I'm not willing to use something like Prey on my android - first time I've heard about the folks, although they might be good, privacy is more important than stolen device which might be encrypted.
Cons:
- AVAST! theft part requires a root to unleash its potential
Happy New Year 2012 Scott and thanks for many good posts - one thing, in gmail you can check your IP history & it even asks security questions once someone logged from different IP than usuall even though you know a password. So you can leave 2-way auth off sometimes.
and bitlocker is great, too bad TPM is scarcity in many new (even business) laptops
For me it's a bit scary to loose my stuff while being stranded in India or similar and not having a way to access my accounts.
- 265AES encryption
- build in keypad
- USB 3
- compatible with any 2,5 or 3,5 drive, no additional case needed
http://usb.brando.com/ezsave-lockdock-usb-3-0-sata-hdd-dock_p02760c057d15.html
I don't have the same cell phone number any more and I can't authenticate on any computer because the 30 day window was perfectly timed. Google keeps sending my codes to the old phone number.
I have tried to recover with their on-line tool about 15 times now...
"Help me, Obi-Wan-Hanselman, you're my only hope!"
Do you know anybody at Google Accounts? you must, you are Scott. ;)
I just don't know what to do...
*When you turn on 2-Step verification PLEASE print out some 'back-up' codes...
Comments are closed.

https://twitter.com/#!/modery/status/154130652634157056/photo/1
While the majority of people here are ethnic Chinese, English is still the language that's used generally for everything.