Hack a TV into a Teams and Zoom Computer with EpocCam and Miracast
If you have a TV, you can turn it into a fancy conference room monitor and pretend you have a Surface Hub 2S. Let's see the different ways we can make Teams/Zoom meetings more a "walking around and thinking" experience, and less a "hunched in front of the laptop" experience.
Cheapest/Good - Wire up to a big TV
You can just get a nice HDMI cable and plug it into your TV and duplicate or extend your laptop's screen. In this simple scenario you're using your Laptop's mic and webcam, and just using the screen of your TV. You can also check your audio output and use the TV speakers as output if you like.
Doing this is not just a nice change of pace, but it reminds you of the options you have to hold meetings! It's your space...how many ways can you change your boring meeting into a new perspective by using the same space in a new way?
Cheap/Better - Wireless to a big TV
If you want to be wireless, you can use Miracast (if your computer/laptop/Surface supports it) or AirPlay or AirServer to "throw" your screen wirelessly to your TV. Some Samsung Smart TV support wireless communications built-in!
- You may be able to throw from Windows to a Smart TV with AirServer software. You may be able to throw with AirPlay on your Mac to an Apple TV.
- You may be able to get a Miracast HDMI dongle (amzn link) and make a dumb TV smart. This is the solution I use. I throw my Surface screen over Miracast to the TV.
Less Cheap/Best (for me) - Wireless to a big TV with a wireless Webcam via my iPhone
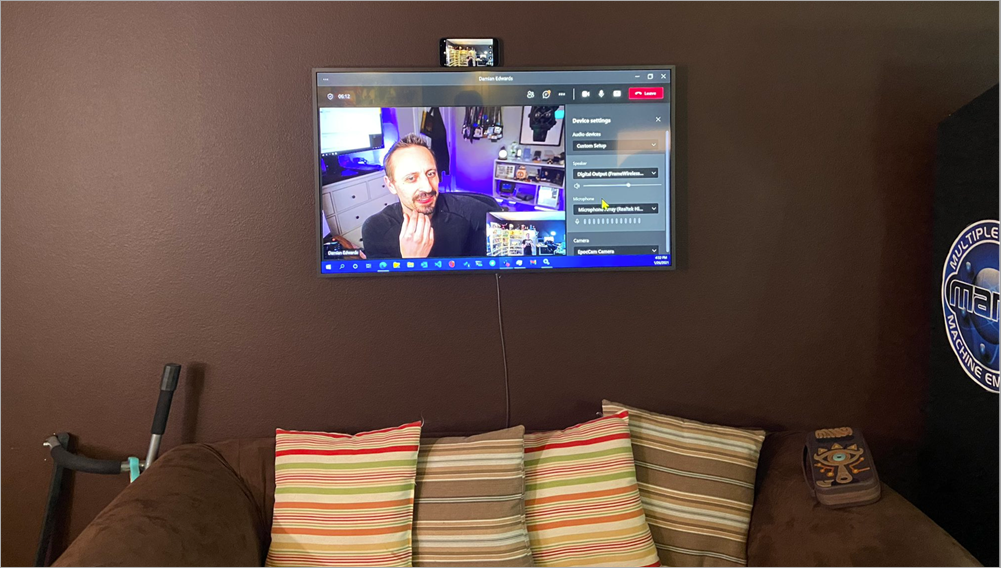
I have a TV on my wall in my office, but it doesn't lend itself to wires and moving my laptop. I wanted to throw the screen over there AND also have a webcam on top of the TV. Ideally there'd be a webcam in the bezel of the TV, but there isn't.
What's an ideal and cheap webcam? My iPhone is already a great device with a long life battery, it's portable, and a webcam. You can get a number of apps that will enable you to use your iPhone (or Android) as a webcam.
I decided on Elgato EpocCom to turn my iPhone into a webcam.
Troubleshooting: The docs aren't amazing, so you'll want to not only install the software, but confirm that the EpocCamService is enabled in the Windows Firewall for both Private AND Public Networks (or ensure your network is the same type as the type that's enabled for this service.) I had to manually allow the EpocCam Service to work on Private Networks.
Then you'll get the iPhone side of the app and your iPhone will show up as a camera. With the Pro version ($7.99) you'll get higher quality and microphone support.
Now I just put my iPhone on the top of the TV, run the EpocCam software, and then on my PC I throw my video to the TV and select the EpocCam virtual Camera. Now I can wander around my office and pace and talk and think, which is great!
Here I've got my Samsung Frame TV (amzn link) (I got it for just $600 as it's the 2018 model, I love it) and I've hooked up the Microsoft Wireless Display Adapter v2 (amzn link).
Other Alternatives
Once you familiarize yourself with these wireless options for throwing video and audio around, you'll find there is no right answer. There's only the answer that works for you! The results will be similar, but some of the solutions will fit better into your system or setup.
Here's some other ideas.
- Use NDI Tools to throw formally throw video around your office and catch it with OBS or XSplit
- Use a really long USB extension code and mount a cheap webcam on the top of the TV
- Just use your iPhone or iPad or Android device and join Teams or Zoom with the phone itself! Then either wired (via adapter and HDMI) or wirelessly connect the device to your TV!
Leave your solutions in the comments!
There also appear to be Teams devices that will take a TV or Display and Teamsify it! I'll go educate myself about those as well!
Sponsor: Protect your apps from reverse engineering and tampering with PreEmptive, the makers of Dotfuscator. Dotfuscator has been in-the-box with Microsoft Visual Studio since 2003. Visit preemptive.com/hanselminutes for a professional-grade trial.
About Scott
Scott Hanselman is a former professor, former Chief Architect in finance, now speaker, consultant, father, diabetic, and Microsoft employee. He is a failed stand-up comic, a cornrower, and a book author.
About Newsletter

 I think we can all agree 2020 sucked. Hopefully 2021 will be better.
I think we can all agree 2020 sucked. Hopefully 2021 will be better.