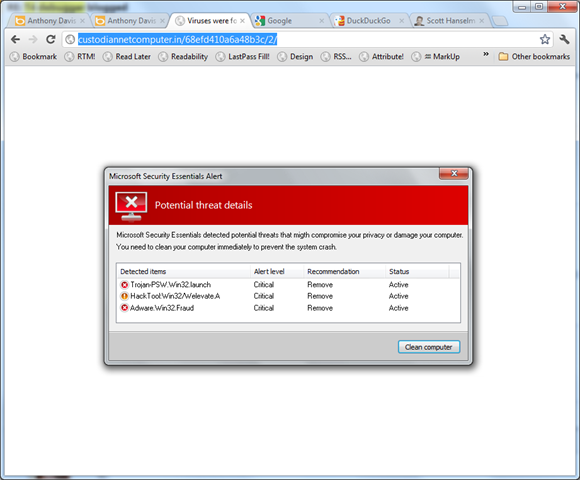
If malware authors ever learn how to spell we're all screwed - the coming HTML5 malware apocalypse
Forgive the lousy screenshot and transparency in the title bar, but I just got this fake virus popup while searching for an image. I admit for a single moment my heart jumped.
Then I thought after a few seconds as a techie (and note that all these observations just happened all at once in my head in no order):
- The dialog is perfectly centered in the browser. I'm not sure why this was my #1 tipoff, but for me, it was the first thing I noticed.
- This "popup" was as a result of a browser navigation. If it were legit I'd expect it to happen a little more asynchronously.
- The word "migth" misspelling in the popup.
- The fonts in the column headers are anti-aliased with one technique and the rest of the text doesn't use ClearType while my machine does.
- Poorly phrased English: "You need to clean your computer immediately to prevent the system crash."
- There's no option other than "Clean computer." No ignore, repair, quarantine.
- The word "computer" at the end of the first line goes too far to the right of the grid's right margin. It should have wrapped to the next line. Yes, I'm a UI nerd.
- Their Aero theme color is GRAY and mine is BLUE.
- Ctrl-Scroll ZOOMs the image. ;)
- The URL is obvious nonsense.
- Adware.Win32.Fraud? Seriously?
It's scary just to look at floating in your webpage there isn't it?
How is my Mom supposed to defend against this? Windows OR Mac (or tablets) the bad guys are out there, and one day they will finally learn English and put a little work and attention to detail into these things.
One day these things won't be "selectable" to prove to us that they are HTML:
As we enable HTML5 with local storage, geolocation, possibly native code and and other features the bad guys will start doing the same with their malware. If you can write Doom in HTML5 there's nothing (except the skill and the will) to keep you from writing adware/scareware/malware in JavaScript. Not just the standard CSRF/XSS type JS - which is bad, I know, I used to be in banking - but sophisticated duplicates of trusted software accurately recreated entirely in HTML5/CSS3 and today's modern JS.
Google Offline Mail and extensions run in the background in my browser now, what's to say some future malware won't? Should we digitally sign HTML5 apps? Do more Extended Validation SSL Certificates? How do you defend against this?
What do you think, Dear Reader?
About Scott
Scott Hanselman is a former professor, former Chief Architect in finance, now speaker, consultant, father, diabetic, and Microsoft employee. He is a failed stand-up comic, a cornrower, and a book author.
About Newsletter
The only way to combat it is education. There will be infections--no doubt about it. But I've trained the people I support to contact me before clicking anything, regardless of the message displayed on the screen.
I don't know about your Mom, but mine would leave it on the screen, take a picture and call me. ;)
http://www.technolog.msnbc.msn.com/technology/technolog/scammers-intentionally-write-lousy-emails-heres-why-837902
[)amien
[)amien
Now being my computer is in English, if I saw this, I would be severely alarmed. But the first thing I would tell my people is:
"Check right next to the clock, if the icon down there is other than green then try grabbing then minimize the browser and deal with it, if it minimizes with the browser.... then it's fake"
I remember when these started to pop up back when vista was new. Its all over again. But this time... it has a little bit more of engineering.
I believe it is mainly a scareware in form of installable application that is a main concern.
The answer is to make sure your family only use sandboxed operating systems.
BINGO!!!
They don't need trigger to fire. We can avoid to visit their site or take it as it is.
For unsophisticated users - Red is bed, Close your browser, OR educate them in this regards.
I'm expecting it to get a lot worse with more and more active content.
In particular, signing all javascript, css and static images certainly _can_ be done. It may require some additions to HTML5 to allow websites to directly pass JSON (embedded in the HTML) to javascript functions without doing this in javascript.
the one CSS for selection is:
::selection {
<put some transparent colors to background and color>
}
for your selection
and as property
* {
user-select: none;
user-drag: none;
}
I think as they get more advanced communication is key, the meta of all user experience will make scammers less effective.
Now if only there was a way to get these old people off of IE6 or Netscape Navigator.
You can do things like these a million ways, e.g. just sending an image attachment to someone's e-mail. What matters is what happens when you click on the link: it probably tries to sell you on something, get your credit card etc, which you must be *extremely* gullible to fall into, and doesn't depend on the fake image at all.
One would be to allow application installs from one place -- what Windows 8 will do and what mobile OSes have been doing for a while.
Another way would be to have some kind of prompt, similar to a UAC prompt, that shows up every time (no exceptions) you're trying to install an application. It has to show up every time for it to work, and it has to do something other apps can't emulate. For example the entire desktop would shrink by 20%, or some other kind of UI clue, or force them to enter a password.
As long as there's a way to trick people, people will be tricked.
it would be an OS Concern!
Else
a Browser Concern
End If
:)
The rule of thumb is not to respond directly to user interface prompts I didn't initiate in some way.
That's certainly impressive scareware, I'd click it!
As I understand it, for the most part, the browser and anti virus companies work in isolation.
An idea would be to have centralised 'malware authority' that holds information on known threats , their domains, spamlists , virus signatures etc.
Web clients and/or antivirus companies then subscribe to this authority, and further, obligated to share threat information with a focus on prevention rather than clean up.
Something along the lines of what the various standards bodies like W3C do. The authority could certify vendors as compliant.
Perhaps such is already in place but I haven't heard about it?
HTML should not be a platform to write applications.
With all web technologies (especially something acient like HTML, DOM, ASP and PHP) young kids learn the anti-patterns of software development and it is the only thing they know.
So they think HTML5 is cool, but there are developer "gods" that created Java or .Net and they should not let "kids" make decision about were the future of development is heading.
It's like incompetent Steve Jobs was telling everyone to start developing web apps for iPhone v1...We know how that turned out...Maybe Microsoft should not have abandoned Silverlight for HTML5 after all :)
So tell your MOM to shut down computer every day ;)
What actually happens if you click Clean Computer on a fully patched Win7 machine with MSE and Chrome as the browser?
Check this screenshot: http://grab.by/etUG
The numerous warnings you saw work as a filter. They improve the conversion rate AFTER the first click by making sure only the most gullible people click through.
See also http://research.microsoft.com/pubs/167719/WhyFromNigeria.pdf
Speaking of web, I spent 2 minutes to find Google's malware submission page (http://google.com/safebrowsing/report_badware) and I think an official extension or a-button-kind-of-thing would be much better. I spent 2 minutes, others wouldn't go for that.
- One day these things won't be "selectable" to prove to us that they are HTML:
Possible to do, has been possible to do since way before HTML5.
- As we enable HTML5 with local storage, geolocation, possibly native code and and other features the bad guys will start doing the same with their malware.
Local storage is isolated on a per domain basis and it essentially a key-value store of strings.
Geolocation will always ask before locating and it will be inaccurate at best (unless device has GPS)
Native code at least currently seems very unlikely to happen across more browsers than one (Chrome) and it's also somewhat isolated as far as I know and will ask questions before allowing anything to run
- sophisticated duplicates of trusted software accurately recreated entirely in HTML5/CSS3 and today's modern JS.
It has been possible to write sophisticated duplicates of software in HTML/JS for quite a long time. It has certainly become more popular as more and more people are online nowadays.
- How do you defend against this?
All browser features such as you outline are designed with security in mind. Of course it's generally implemented as a box which asks the user whether or not they want to allow that
So in the end the security is only up to user education. Never accept anything you're not sure of.
Any good web developer could do a nearly perfect replication without the flaws you mention. Thankfully it seems malware authors are not good web developers...
On a side note, I love these "Oh no HTML5 is bad because it allows you to do this" comments...
@Matt- you nailed it. My mom can run circles around my dad in computer literacy. Mom can smell when something's not right, dad, not so much. About 2 months ago, someone called and said the computer had a virus or some such (dad picked up). He told mom to not touch the computer because of it, but mom inquired and told him that it was a total fake.
@pfs - your world is a very gloomy place isn't it?
Yes, there are plenty of older dads out there too who know little about computers. But now we're edging towards being AGEIST aren't we?
Scott's choice of target demographic for illustrative purposes is broadly true.
Does anyone know if there is a browser for it?
If you (or Mom) had the Web of Trust installed, this is what you would have seen when visiting an evil site like this. I'm installing this free tool on Mom's machine today. It's a browser plugin that uses other people's experience to augment yours!
http://www.hanselman.com/blog/WhatGeeksNeedToTellOurParentsAboutShoppingOnlineSafelyAndSecurely.aspx
But I have another idea. What if Windows put a user identity icon in window's title bar of every window that gets opened? In that case every window would have your own account image (or your image with some shortcut-like mini icon to system process running windows). That way these images could never have the correct image displayed and users would know that this window is not opened by their OS.
Another question for you Scott: You say that the browser centered image was the giveaway in your case. You browser wasn't in the maximized state then was it? Otherwise it would seem to be screen centered at least in horizontal space.
Window with identity on http://i.imgur.com/qDPNl.png
This identity image could as well be almost completely transparent and when you'd be getting closer to it it would become more opaque also displaying your username or become bigger or something.
This would be jolly hard for malware authors to replicate. The effects can yould be yes, but not the image or name. And this could then be a system-wide solution.
But honestly, spelling aside, it's bound to happen to Mom, Grandma or even Uncle Leo. Facebook has over 900,000,000 users. If I were to write anything, I would like at FB as the doorstep to 900,000,000+ homes world wide. You can send it to millions, and all it takes is a few people that doesn't know any better.
#SadTruth
"You need to clean your computer immediately to prevent the system crash."
I admit it doesn't jump off the page, but the big thing for me is "the system crash." If anything, it should be "a system crash."
Also, the wording is lazy. "clean your computer." Really? Like get out a bottle of window cleaner and some paper towels?
I started to write a better sentence, but I don't think I need to aid malware developers, but I'm sure if you give it some thought you could come up with something more legit sounding.
@Robert Koritnik - I think your idea is an excellent one. Something needs to be build into the OS itself that clearly identifies real windows from fake ones. Custom security images are already used in many online banking sites when logging in so the concept should be familiar to most users.
This just shows that HTML was never intended to be an application platform. But now that it's being forced to be one, it's almost like we've moved backward in time, forced to re-address problems that were already addressed years ago.
This way, my mother could select a photo of say, her granddaughter at Easter, and any time she gets a popup she knows that unless she sees her cute little granddaughter in her Easter dress, that the message is likely a fraud, and she should not listen to anything it says.
But as Scott said, changing your default window color goes a long way to making frauds easier to spot. I hope Microsoft never removes 100% of the UI customization options in Windows.
I'm liking Apple's idea of developer certificates on OSX Mountain Lion (Gatekeeper) and vetting apps in the App Store. Also Windows 8 is getting an App Store. If both systems allow some way to force only software from App Stores, or from signed certificates, that would go along way to stopping this*
* I know the new OSX allows you to force App Store & signed apps only, and stop the installing of unsigned/non-verified apps (http://www.macworld.com/article/1165408/mountain_lion_hands_on_with_gatekeeper.html). One of the reason I'm trying to get my parents to buy a Mac, I could set this option and not worry about them getting virus. Hopefully, Windows 8 introduces a similar option.
It seems like something similar could be built into the OS UI that would show you information that could help determine how "legit" a window is. What process is it running under? What directory is the executable in? When was it installed? Maybe "where did this come from?"
Might not be enough to help mom figure out if something like this is real, but at least if she gives you a call it would give you enough clues to determine if it is bogus.
1. Choose a language other than English. Preferably some obscure dialect.
2. Create some kind of hideous theme with the most terrible colors you can come up with.
Any fake notification will stand out in your desktop.
Now THAT will give those scammers a very hard time ;)
I think the scam went something like this:
1. Legitimate websites are infected with malware that redirects users coming from certain sources (like google) to another page that shows this popup (this reduces the chances that the site owner will actually notice the infection, since they probably visit the site only by direct URL).
2. The user clicks "Clean computer".
3. The webpage uses browser vulnerabilities to install some malware on his/her computer.
4. The malware is essentially the same thing: it pops up every 5 minutes (very annoying) telling that is has found a virus (this time it's a real windows-popup). But this time to clean your computer you have to "buy the full version" of this software. So the user is scammed into giving away money, and possibly their credit card information. I don't know if you actually get rid of the popup that way, but the whole process is made to look as legitimate as possible and will probably fool most not-so-tech-savvy people.
Step 3 is something that should never happen. Yet, in our case the computer that got infected was a work laptop, which was restricted to IE 8, and where the user didn't even have permissions to install anything herself (yet a website seemed to have no problems doing so). The latter also prevented me from removing the malware myself, and the laptop had to be fixed by the company's IT staff, which probably took weeks.
There's a lesson in there somewhere ;)
If you search some picture on Bing.com, then click on the thumb to preview; you will automatically redirect to the malware page:
hxxp://scankeeperguarantor.pl/68efd410a6a48b3c/pr2/2/
Be careful to open the above link.
An example bing link:
hxxp://www.bing.com/images/search?q=todictionary&view=detail&id=047B96ED97DBA8AD5A11480E021747EE010DE568&FORM=IDFRIR
Anything wrong with BING.com,or my computer? :P
There have always been shysters and conartists. They just adapt to new environments. They exist in the net and outside of it. We educate ourselves or protect ourselves and others from them but they just find new ways. It will be a never ending battle.
Just customize your gui. I have mine like the old pascal editor...lol
So i only click yellow text on a blue page !
Blocked domain at work and reported it to Google.
If you're seeing this type of behavior on your site and you serve up 3rd-party ads, you may want to contact your ad provider and see if they're have been reports of this aberrant behavior from other customers.
http://securitywatch.pcmag.com/none/299326-mlb-com-serving-fake-antivirus-via-malicious-online-ads
... focus follows mouse.
Or if you don't want to change focus, maybe add a distinguishable border to the content canvas of the current window... eg. in pseudo-html... body:active {border: #FF0000 2px;}
while the border is visible, you're actually interacting with content within a browser session.
Real popup windows could point out their origin in their title bar.
Comments are closed.