Using WSL and Let's Encrypt to create Azure App Service SSL Wildcard Certificates
There are many let's encrypt automatic tools for azure but I also wanted to see if I could use certbot in wsl to generate a wildcard certificate for the azure Friday website and then upload the resulting certificates to azure app service.
Azure app service ultimately needs a specific format called dot PFX that includes the full certificate path and all intermediates.
Per the docs, App Service private certificates must meet the following requirements:
- Exported as a password-protected PFX file, encrypted using triple DES.
- Contains private key at least 2048 bits long
- Contains all intermediate certificates and the root certificate in the certificate chain.
If you have a PFX that doesn't meet all these requirements you can have Windows reencrypt the file.
I use WSL and certbot to create the cert, then I import/export in Windows and upload the resulting PFX.
Within WSL, install certbot:
sudo apt update
sudo apt install python3 python3-venv libaugeas0
sudo python3 -m venv /opt/certbot/
sudo /opt/certbot/bin/pip install --upgrade pip
sudo /opt/certbot/bin/pip install certbot
Then I generate the cert. You'll get a nice text UI from certbot and update your DNS as a verification challenge. Change this to make sure it's two lines, and your domains and subdomains are correct and your paths are correct.
sudo certbot certonly --manual --preferred-challenges=dns --email YOUR@EMAIL.COM
--server https://acme-v02.api.letsencrypt.org/directory
--agree-tos --manual-public-ip-logging-ok -d "azurefriday.com" -d "*.azurefriday.com"
sudo openssl pkcs12 -export -out AzureFriday2023.pfx
-inkey /etc/letsencrypt/live/azurefriday.com/privkey.pem
-in /etc/letsencrypt/live/azurefriday.com/fullchain.pem
I then copy the resulting file to my desktop (check your desktop path) so it's now in the Windows world.
sudo cp AzureFriday2023.pfx /mnt/c/Users/Scott/OneDrive/Desktop
Now from Windows, import the PFX, note the thumbprint and export that cert.
Import-PfxCertificate -FilePath "AzureFriday2023.pfx" -CertStoreLocation Cert:\LocalMachine\My
-Password (ConvertTo-SecureString -String 'PASSWORDHERE' -AsPlainText -Force) -Exportable
Export-PfxCertificate -Cert Microsoft.PowerShell.Security\Certificate::LocalMachine\My\597THISISTHETHUMBNAILCF1157B8CEBB7CA1
-FilePath 'AzureFriday2023-fixed.pfx' -Password (ConvertTo-SecureString -String 'PASSWORDHERE' -AsPlainText -Force)
Then upload the cert to the Certificates section of your App Service, under Bring Your Own Cert.
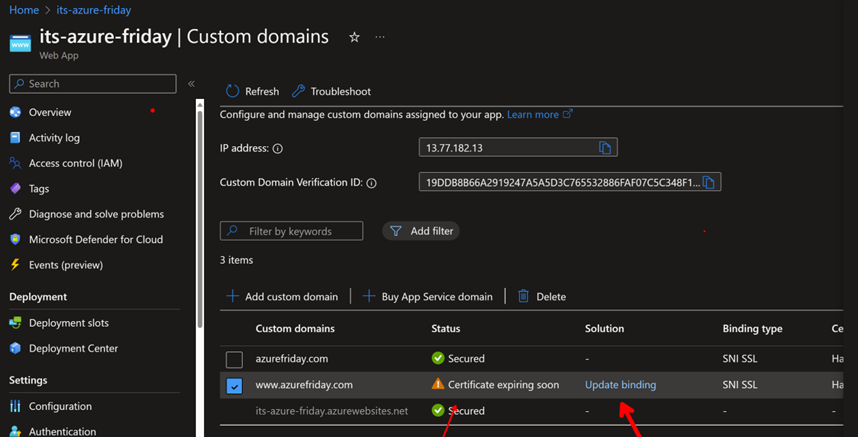
Then under Custom Domains, click Update Binding and select the new cert (with the latest expiration date).
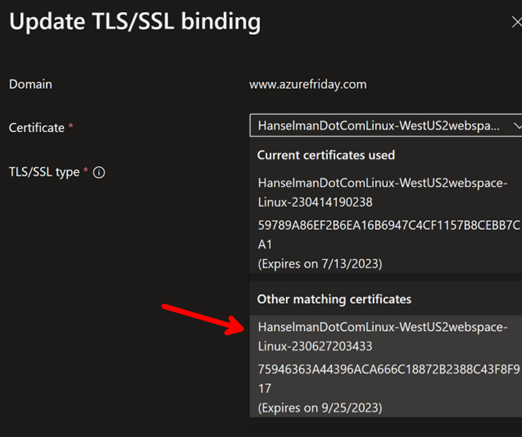
Next step is to make this even more automatic or select a more automated solution but for now, I'll worry about this in September and it solved my expensive Wildcard Domain issue.
About Scott
Scott Hanselman is a former professor, former Chief Architect in finance, now speaker, consultant, father, diabetic, and Microsoft employee. He is a failed stand-up comic, a cornrower, and a book author.
About Newsletter
regarding further automation ;) have you looked at Lego (https://go-acme.github.io/lego/)? It's a Go client (also offers Windows binaries, including ARM) and has several DNS providers included. So given Azure credentials it can solve the DNS challenges automatically for you. And of course it has an option to run a script after the certificate was renewed (so with your Powershell skills it should be fairly easy to upload the certificate to azure to have everything automated...)
Comments are closed.

Thanks for the instructions.