Windows 7 with BitLocker and Still Booting To VHD
 As a remote worker at Microsoft I have to deal with a few little things that the average worker in Redmond doesn't.
As a remote worker at Microsoft I have to deal with a few little things that the average worker in Redmond doesn't.
For example, none of my machines are wired to "CorpNet." They're all remote so for the last two years I've had to RAS (Remote Access Service) into the corporate network. For a while you could use your password, but then you needed to use your Smart Card (or your immortal soul, as I call it) and a complex pin. So you've got multi-factor authentication, you need your actual network password (and of could your domain\username), your physical smart card and your smart card's pin. That's a lot. Someone evil could have two of those three things and you'd still be OK.
Since two of my three machines are laptops, there's always risk that I could lose it or have it stolen. If I kept secret stuff on my laptop (I don't) that could be a problem. Laptops run Windows 7 now and are required to be BitLocker'ed (FAQ). This means the whole hard drive is encrypted, there's an (optional) PIN to even turn it on, and it can take advantage of newer machines that have a TPM (Trusted Platform Module). Basically a TPM is a hardware cryptoprocessor that can store keys for securing information. BitLocker uses this chip to project the keys and makes sure the BIOs and boot sector haven't been tampered with. Fortunately it's all automatic so I don't have to think about it.
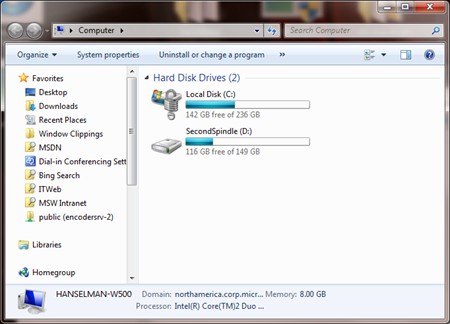
This is what I see when I'm booted off my Bitlocker'ed C: drive. That D: drive is my other spindle.
I recently Bitlocker'ed both my laptops, but I Boot to VHD for many demos and it's not possible to boot off a VHD that lives on a Bitlocker'ed volume. That's the one bad thing about Bitlocker from my point of view. I'm sure it's a chicken and the egg problem. How do you boot off a file on an encrypted volume without booting off the encrypted volume?
Turns out though that you can still Boot to VHD in a few other ways. You can partition your drive with a Bitlocker'ed C: and an unencrypted D:, or you can get a second spindle. That means, you can get another hard drive and put it in the slot when your DVD/CD usually goes. That's what I decided to do.
I bitlockered my 256 gig OCZ Vertex SSD, and I have a D: drive that is my 160 gig random no-name SATA drive. On that drive I only put demo VHDs.
I had to go into the BIOS of my Lenovo W500 and add the drive to the "boot order" in order to make it spin up on boot and be available to Windows. Then, since I can't really be sure of it's drive letter that early, I changed the syntax of my BCDEdit settings a bit. Figured I'd let Windows figure it out, so instead of [D:] I used [LOCATE]. Like this:
C:\>bcdedit /copy {current} /d "My New VHD Option"
C:\>bcdedit /set {guid} device vhd=[LOCATE]\<directory>\<vhd filename>
C:\>bcdedit /set {guid} osdevice vhd=[LOCATE]\<directory>\<vhd filename>
C:\>bcdedit /set {guid} detecthal on
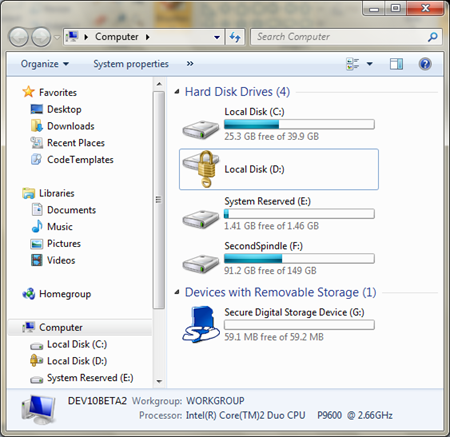
Now, when I'm booted into my VHD, I see this:
What are we seeing?
- My D: drive is my original boot SSD. It's marked with a lock icon. I can't access it right now.
- My C: drive is the whatever.vhd that I booted off of. I made it 40gigs, so it is. (The actual file is 15gigs, but it "blows up" while I'm running on it. It'll shrink back down when I'm not booted off it.
- My E: drive is some system partition I don't know about.
- My F: is the Second Spindle that all my VHDs live on.
But, how can I get access to my secure C: drive when I'm booted into this insecure world? Of course, we don't want the bad guys to get in there, which makes sense.
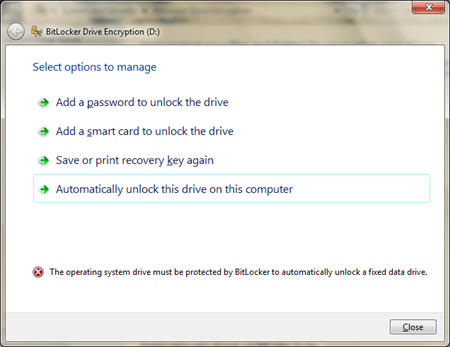
If I double click, I see this:
These options are all settable with Group Policy I think, but my choices are to add a really complex Password to get access to this drive or use my Smart Card. I can also use the recovery key that I saved in a secure location when I originally locked the drive.
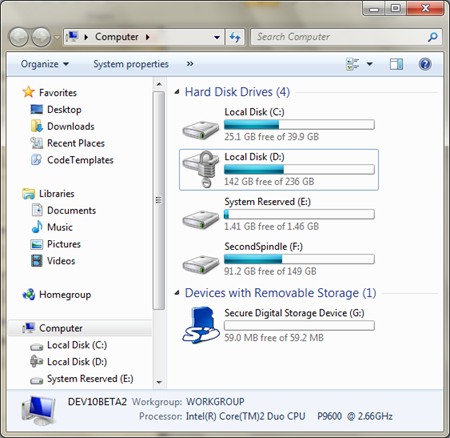
I unlock it, and I see this:
Now, just for the duration of this single boot, this disk is available to me. Very cool.
I was a little afraid when I Bitlocker'ed my machine just before a trip, but I'm feeling pretty good about it so far. I haven't noticed any perceptible slowdown but the FAQ says "single digit." I've heard numbers like 3%, but I haven't noticed it in the sense that my machine isn't suddenly "sluggish."
I'm VERY suspicious when corporate IT wants to reach out from Redmond and do something to my computer but this turned out great.
Here's the email I sent internally to my team today about Bitlocker:
As you know, MSIT is starting to put BitLocker on mobile machines. I recommend you upgrade any Vista machine to Windows 7 before running Bitlocker. As always, backup your data first.
I figured I should be the guinea pig for you guys, so I Bitlockered BOTH my Lenovo T60p and Lenovo W500 yesterday. These are my two corporate machines.
1a. On my W500 I was automatically prompted to reboot and enable the TPM (trusted platform module) in my BIOs. This enable step was automatic and only required me to press F10 once.
1b. On my T60p, I was told to enter the BIOs manually and enable it. There is no “TPM” section in the T60p. Instead, you go into Security, the Security Chip and turn on all the options under Security Reporting. Save your BIOS settings and reboot.
2. When prompted for a “PIN” I declined. This >=5 digit number would be a system-level password for when you start-up your machine. It's recommended, but ultimately up to you.
3. The process ran OVERNIGHT. It took at least 5 hours on each machine from what I can tell.
4. Next, go to the Start Menu and type “manage bitlocker.” You’ll want to save and print your recovery key. The Importance of this step cannot be overstated. Save this key and treat it like it is your immortal soul.
c. If Bitlocker smells any funny business you’ll get prompted for these keys. Murphy’s Law says this will happen 10 minutes before a major conference speech. No excuses for not having these. Without them, your computer is a brick. (That's kind of the wonderful point of BitLocker. ;) )
That scary part said, it works exactly as it should. It was easy and painless.
So far, we are not forced to lockup second drives/spindles. This means that you can STILL boot to VHD off of a second drive if that drive is NOT connected via USB (SATA, IDE, etc are still Ok). I’ve moved my BootToVHDs off into D:\ for this purpose. Regular VMs run just fine on the BitLocker'ed drive.
All in all, it works exactly as it should. I have no idea it’s there and my machine seems just as fast.
Let me know it you have any questions.
All in all, an interesting experience. I'm glad it went so well. You can even BitLocker USB drives as well with BitLocker To Go.
Related Links
- Less Virtual, More Machine - Windows 7 and the magic of Boot to VHD
- Step-By-Step: Turning a Windows 7 DVD or ISO into a Bootable VHD Virtual Machine
- Windows 7 Screencast – BitLocker To Go
- BitLocker area on technet.microsoft.com
- BitLocker Technical Overview – the must read
- BitLocker Interview and demos on edge.technet.com – a really good overview created by Adam Bomb.
- KB Article on the BitLocker Drive Prep Tool
- Windows 7 Dual Boot with Bitlocker
About Scott
Scott Hanselman is a former professor, former Chief Architect in finance, now speaker, consultant, father, diabetic, and Microsoft employee. He is a failed stand-up comic, a cornrower, and a book author.
About Newsletter
Pausing Bitlocker takes seconds, and is different from removing it and reapplying it. Plus, you just need to keep your recovery key with you if it does trigger. A good rule of thumb is to pause BitLocker on any major operation or install. That's overkill, but safest.
Kind of defeats the purpose, does it not? I will use hardware based self encrypting disks (SED) as defined by the Trusted Computing Group (TCG) anytime over BitLocker. No hassle setting it up. It just works out of the box.
As I understand it, WHS saves the data unencrypted.
http://blogs.msdn.com/microsoftbob/archive/2009/01/04/windows-home-server-and-backups-for-the-paranoid.aspx
Obviously someone is more likely to steal your laptop in an airport rather than steal a WHS from your house but still...I'm curious what their dogfooding opinion is regarding this...
Dave - No, there's multiple levels. They could have my drive and smart card, but would need my SmartCard pin/password. Also, there can be a bootup pin also.
Michael - Agreed, if you can replace the hard drive with a Encrypting drive. However, there's a lot of drives out there (like the ones that 80,000+ MS employees use) as well as my new $600 OCZ Vertex SSD. This is a good solution for those existing drives.
My company uses PGP Desktop whole disk encryption and i think this is causing a problem similar to that described here. My problem is that although the drive is actually unlocked by the PGP boot process, at some point during the bootup of the VHD it bluescreens. I think i would possibly be ok if i could just find a way to insert the relevant PGP drivers into the VHD image and make the necessary changes in the registry of the VHD image so the drivers were loaded. I think this is my chicken and egg issue :-)
"If Bitlocker smells any funny business you’ll get prompted for these keys. Murphy’s Law says this will happen 10 minutes before a major conference speech. No excuses for not having these. Without them, your computer is a brick."
Right on. To add to this it seems quite obvious, but I always tell those individuals setting up BitLocker to not leave the USB with the keys plugged in to the machine or lying around, as it is like leaving the keys to the car on the hood. But on the flipside, they can't be too far away; an alternative.... memorize the keys from the print out. Yeah right!
Also, if anyone comes across this and needs just the details on making your drive 'Bitlocker'ed' (as Scott called it :) ), check out the following detailed post:
How To: Set Up BitLocker Full Disk Encryption + Pre-Boot Pin in Windows 7 Ultimate:
http://allen-conway-dotnet.blogspot.com/2010/01/how-to-set-up-bitlocker-full-disk.html
This details the actual setup of BitLocker which may also be helpful to those with a single system partition, or just initial setup. There seem to be lots of walkthroughs on TechNet, but I had to piece several together to get the 1 needed recipe. Thanks again for the info!
I know this question is probably not relevant to the blog post, but given that there are some good exchange of bitlocker related information, I thought I could seek some expert advise here as I had tried google for answer but to no avail.
I had recently try to bitlock my primary partition that's currently running Windows 7 64bit Ultimate edition. I have a primary disk, partition into 3, C: & D:, (both NTFS) with the third partition being EXT4 format running Ubuntu OS. I uses Windows 7 boot manager, to boot to Windows 7 and Ubuntu. I wanted to bitlock the partition C:, so I turn it on, and the setup wizard was basically smooth and the system went into the encryption phase. At about 25% of the encryption process, I got a pop up dialog that says "The disk has one or more errors, run chkdsk /r and if the error still persists, it might indicate hardware failure".
I did a chkdsk /r twice (each time it'll be reboot into console and check), but after that, when the encryption process restarts, it'll pop up with the same error again.
I am not sure if it has to do with the dual boot but I don't think so since it's still running Windows bootmanager. Can you think of the possible cause of the problem, other than suggesting that the hardware is faulty (which is unlikely as I have done some disk check, and there's no indication of problem) and the net doesn't have any good advises on this.
Appreciate your help here!
Please provide me proper steps.
Thanks a lot in advance ! :D
Comments are closed.

BTW: How did you manage to alter your BCD without having to remove and reapply BitLocker? I was under the impression that all changes to the BCD resulted in triggering BitLocker.
On a completely unrelated note: altering your system language (f.e. from English to Dutch in my case) will result in triggering BitLocker as it changes your BCD.